Products
Services
June 14, 2018
Cybersecurity has become a huge factor in everyday life. Anyone who uses computers, internet, or credit cards – from individuals to big corporations – is in danger of having their information stolen every time they go online. For any US business, it is imperative to have someone watching and in charge of cybersecurity. The company should also have plans and training for employees to help prevent a breach of the defenses. For medical practices and hospitals, the same is true, but there is also the spectre of HIPAA violations lurking around every corner.
One reason that the small to medium business (SMB) may become a target of cyber threats is because they may not be taking the security steps that a larger business does. An article in Forbes shows this clearly:
“Do you think your small business is at risk of being hacked? An overwhelming 87% of small business owners don’t think so. But, your business might be at risk more than you realize. About half of small businesses experience a cyber attack.”
If a hacker is able to break into a business network, they have the immediate benefit of any financial information they find. And if this is an SMB in the medical field, they might gain access to the HIPAA data of patients that can then be used to create false identities and credit cards.
Additionally, that SMB may be part of the supply chain for a larger business – so now the hacker has a lever with which they might gain access to even richer pickings. The SMB does not want this to happen – the HIPAA Breach Notification Rule for over 500 patient records, “…requires covered entities to notify affected individuals, HHS, and … the media of a breach of unsecured PHI…” (17). Nobody wants to notify their customers and the media that they messed up thereby confirming that they cannot be trusted, to say nothing of giving Homeland Security even more reason to look over their shoulder.
There are large companies in the news, it seems like every other day, that have had hackers break into their systems and access the personal data of millions upon millions of their customers. Big names like Target and Anthem have violated the trust of their customers in this way. This type of exposure on the evening news is something we all want to avoid. As for those in the medical fields, the HIPAA Journal suggests that “if your organization has not implemented the appropriate safeguards to protect the health information of patients and plan members, now is the time to take action. Non-compliance carries a significant cost.” Their infographic (below) gives an idea of that cost.
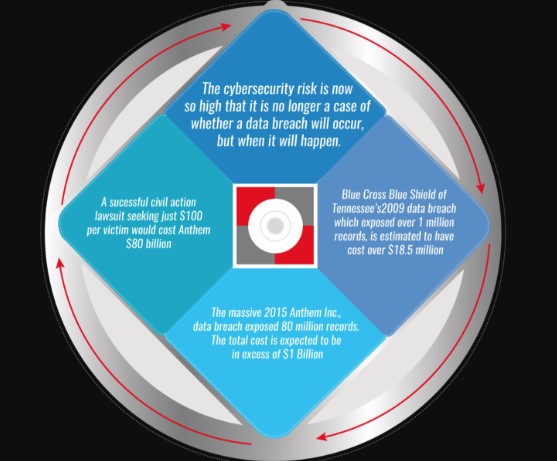
The government fines that you might incur along with other incidentals coming to an estimated $380 per breached record. The breaking news companies are large, often with multi-million dollar cyber budgets. This is because the hackers get more inventive every day. A small company might wonder how to cope with this threat. Nevertheless, they must take planned steps immediately. Data shows that over half of the smaller business breached in this way actually go out of business within six months of the breach.
Here are some minimum steps that should be taken by businesses of any size to better defend against cyber attacks. This may not stop a persistent/creative hacker, but it will block out most and as an added bonus it will put you in compliance with some regulatory security requirements.
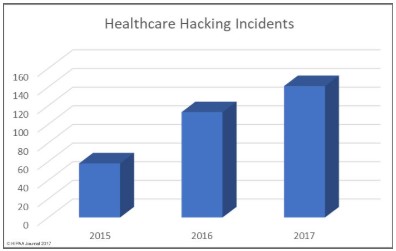
Don’t get caught leaderless and directionless in the face of a crisis that you know is coming. Make a plan and take action on cybersecurity. Your plan to protect your company and your customer data does not need to be grand or complicated, but you have to have one.

Author Bio:
Steve Medeiros is a writer for TechnologyAdvice.com. He has an extensive background in technology, software, and customer support. Find him on LinkedIn.
Bibliography
[/vc_column_text][vc_single_image image=”9683″ img_size=”full” alignment=”center” onclick=”custom_link” link=”http://go.chartlogic.com/webinar/mips-2018-review”][/vc_column][/vc_row]